Hak5 LAN Turtle SD + Field Guide
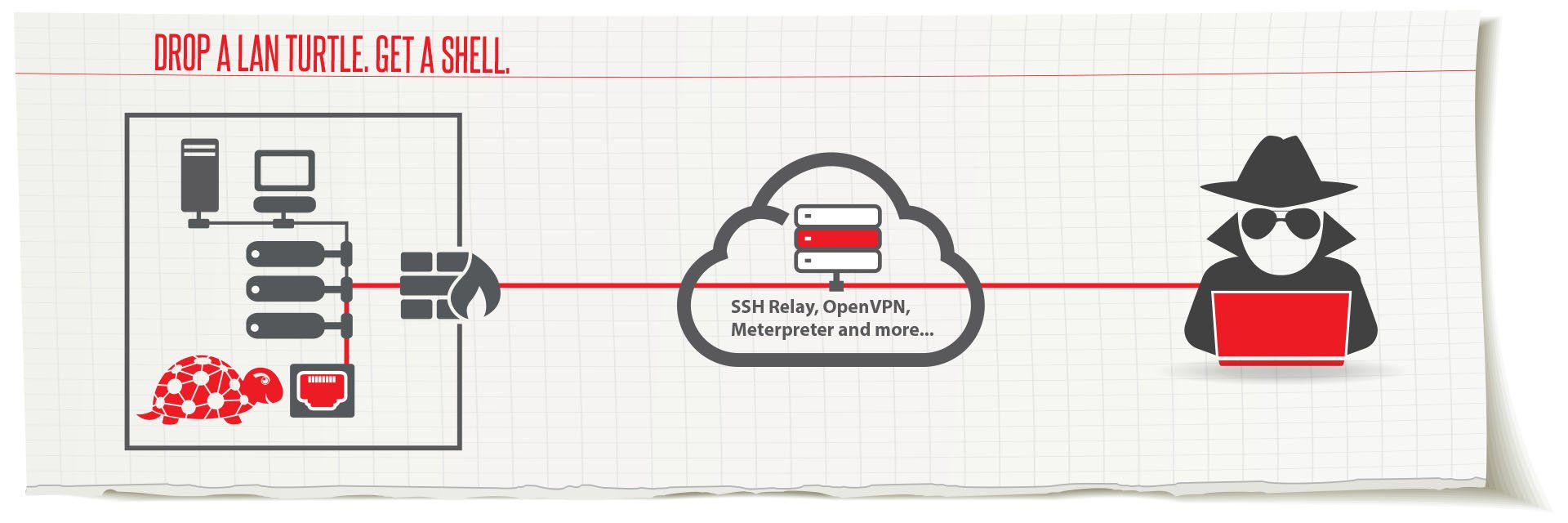
LAN Turtle is a hidden network monitoring, remote access and MITM tool.
| Category: | HAK5 Implants & Remote Access |
|---|---|
| EAN: | 811342030019 |
The LAN Turtle is a covert Systems Administration and Penetration Testing tool providing stealth remote access, network intelligence gathering, and man-in-the-middle surveillance capabilities through a simple graphic shell.
Housed within a generic "USB Ethernet Adapter" case, the LAN Turtle’s covert appearance allows it to blend into many IT environments.
MAN-IN-THE-MIDDLE WITH MASSIVE STORAGE
With man-in-the-middle tools built in, you can gobble up all of the interesting data. Supports massive storage options from the MicroSD card reader hidden inside.
Save heaps of network traffic, or load it up with all your favorite pentest tools.

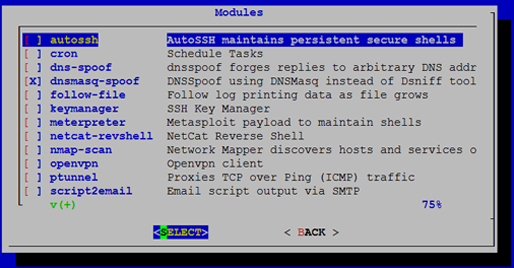
Setting up a reverse shell for persistent remote access is just a matter of checking a few boxes.
With a repository browser built-in, getting more modules is automatic.
Or write a modules with the simple API.
CLOUD C2 READY
Pentest from anywhere online with the free self-hosted Cloud C2. Exfiltrate loot and pivot through the LAN with ease. Even drop into a root shell right from your web browser for full access to the entire LAN Turtle arsenal.

PENETRATION TESTERS
- Pivot with a persistent Meterpreter session in Metasploit
- Scan the network using nmap
- DNS Spoof clients to phishing sites
- Exfiltrate data via C2EXFIL or SSHFS
- Man-in-the-Middle inline computers capturing browser traffic
SYSTEMS ADMINISTRATORS
- Access to the entire LAN through a site-to-site VPN
- Automate management scripts with hourly email reports
- Receive alerts based on defined network traffic
- Maintain remote access with Cloud C²
- Quickly gather pcap (packet captures) files
Notice
This device is designed for experienced professionals in the field of IT administration and IT security. Its use requires the expertise and consent of the infrastructure owner.
Introducing the LAN Turtle by Hak5
Be the first who will post an article to this item!














